AFL-Fuzz training笔记
libxml2
根据afl-training先下载对应版本的libxml2:
git clone https://github.com/GNOME/libxml2.git
cd libxml2
git submodule init
git submodule update
git checkout v2.9.2
|
然后编译:
CC=afl-clang-fast ./autogen.sh
AFL_USE_ASAN=1 make -j 4
|
harness.c
#include "libxml/parser.h"
#include "libxml/tree.h"
int main(int argc, char **argv) {
if (argc != 2){
return(1);
}
xmlInitParser();
while (__AFL_LOOP(1000)) {
xmlDocPtr doc = xmlReadFile(argv[1], NULL, 0);
if (doc != NULL) {
printf("read sucess!\n");
xmlFreeDoc(doc);
}
}
xmlCleanupParser();
return(0);
}
|
编译harness:
AFL_USE_ASAN=1 afl-clang-fast ./harness.c -I libxml2/include libxml2/.libs/libxml2.a -lz -lm -o fuzzer2
|
afl-fuzz -i in -o outputs -x /home/fuzzer/AFLplusplus/dictionaries/xml.dict ./fuzzer @@
|
漏洞点:
在dict.c:1093位置调用宏:
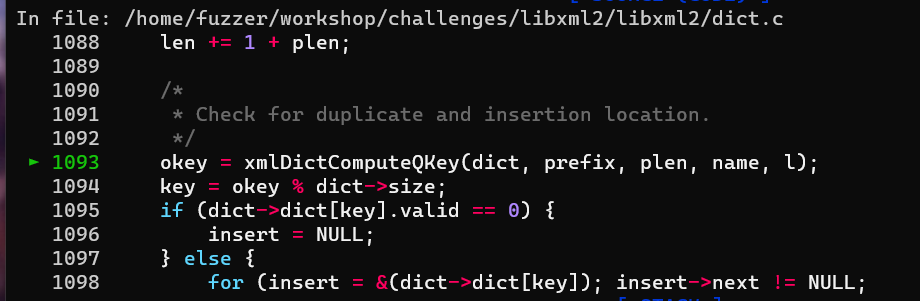
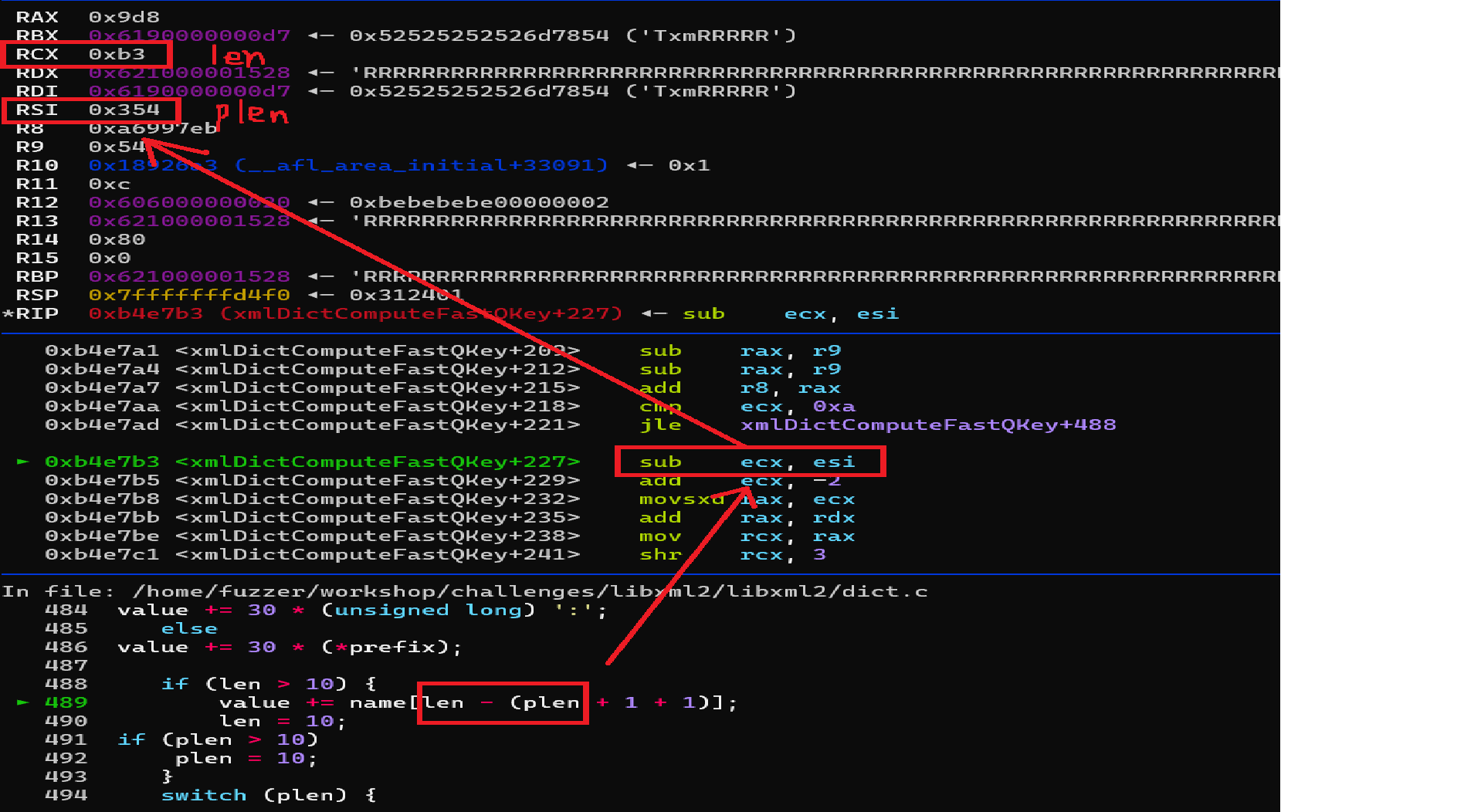
进入到 489 出现数组越界 len = 0xb3 plen = 0x354 ,数组下标为len - (plen +1 + 1) = 0xFFFFFD5D
这漏洞就是CVE-2015-7497
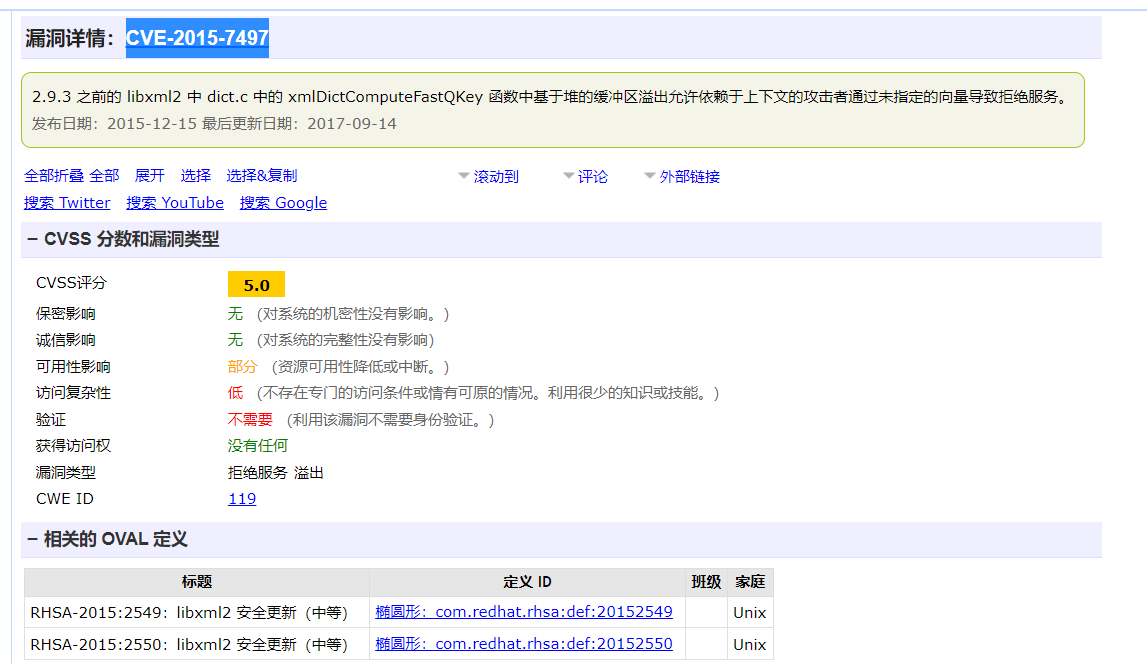
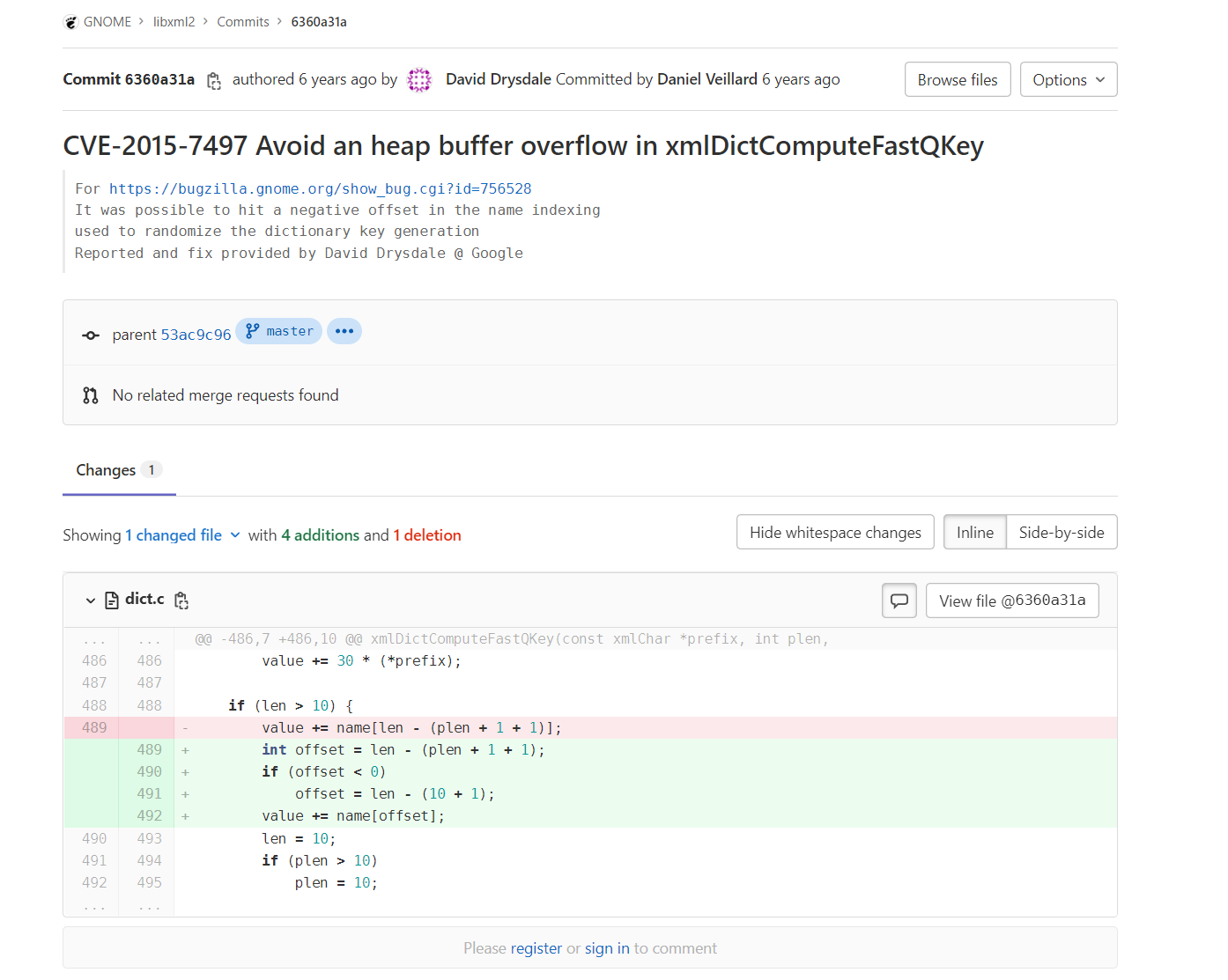
该漏洞在2.9.3的版本中被修复
#include "libxml/parser.h"
#include "libxml/tree.h"
#include <unistd.h>
__AFL_FUZZ_INIT();
int main(int argc, char **argv) {
#ifdef __AFL_HAVE_MANUAL_CONTROL
__AFL_INIT();
#endif
unsigned char *buf = __AFL_FUZZ_TESTCASE_BUF;
xmlInitParser();
while (__AFL_LOOP(1000)) {
int len = __AFL_FUZZ_TESTCASE_LEN;
xmlDocPtr doc = xmlReadMemory((char *)buf, len, "https://mykter.com", NULL, 0);
if (doc != NULL) {
xmlFreeDoc(doc);
}
}
xmlCleanupParser();
return(0);
}
|
删除重复crash seed:
ASAN_OPTIONS=abort_on_error=1:symbolize=0 afl-collect -d crashes.db -e gdb_script -r -rr ./out2/default/ ./collect2 -- ./fuzzer @@
ASAN_OPTIONS=abort_on_error=1:symbolize=0 cwtriage -root ./out2/default/crashes/ -match id -- ./fuzzer @@
|









